As artificial intelligence (AI) continues to reshape the cyber landscape, the complexity and stakes of the intelligence contest between attackers and defenders have reached unprecedented heights. In this dynamic, multi-dimensional conflict, hypergame theory emerges as a powerful framework for understanding and navigating the strategic interactions between AI-driven adversaries and defenders.
Understanding Hypergame Theory
At its core, hypergame theory is a mathematical and strategic framework that acknowledges the different perceptions, beliefs, and understandings that each player (or adversary) holds in a conflict. In the cyber domain, especially with the introduction of AI, players often operate with incomplete or inaccurate information about their opponents' strategies, perceptions, and decision-making processes. This is particularly true as autonomous agents and adaptive algorithms evolve tactics rapidly, exploiting hidden vulnerabilities and creating an environment of extreme uncertainty and unpredictability.
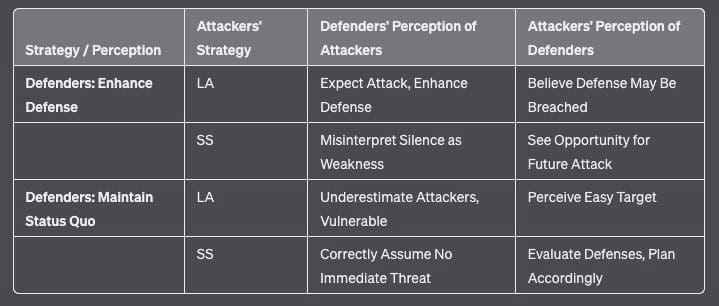
Real-World Applications
Hypergame theory can provide valuable insights into the complex, multi-level nature of interactions in the AI-driven cyber intelligence contest. Defenders must not only anticipate and counter their adversaries' observable actions but also strive to understand and manipulate their underlying perceptions, beliefs, and decision-making processes. This requires a proactive, deceptive approach that leverages AI-powered tools and techniques to create false narratives, mislead adversaries, and shape the information environment to one's advantage.
For example, cybersecurity teams might deploy decoy systems or "honeypots" that appear to contain valuable data but are designed to detect and analyze unauthorized access attempts. Such tactics can mislead attackers into revealing their methods and objectives, allowing defenders to strengthen their actual systems' defenses.
Challenges and Opportunities
The challenges in this AI-driven security landscape are immense. The pace at which AI technologies evolve means that defenders must continuously adapt their strategies. Hypergame theory helps by providing a structured way to anticipate possible moves from adversaries who may not have complete information. This anticipatory capability is crucial in countering sophisticated cyber threats that leverage AI for attack automation and strategy development.
However, the opportunities are equally significant. By embracing a proactive, deceptive mindset and leveraging the power of AI, defenders can gain a critical edge in this high-stakes game of perception and decision-making. This approach allows defenders to not only respond to attacks but to anticipate and preempt potential threats, thus enhancing overall security posture.
Ethical and Legal Considerations
While the use of deception and manipulation in cyber defense is strategically beneficial, it raises important ethical and legal questions. The implementation of deceptive tactics must be carefully managed to avoid collateral damage, such as inadvertently harming innocent parties or violating legal standards. Cybersecurity professionals must balance the need for effective defense strategies with ethical considerations, ensuring compliance with legal frameworks and industry best practices.
Conclusion and Future Directions
In conclusion, hypergame theory offers a robust framework for navigating the complex and evolving landscape of AI-driven cyber intelligence. As AI technologies continue to advance, the application of hypergame theory in cyber defense will likely expand, providing new tools and strategies for securing digital assets. Future research and development in this field will focus on refining these strategies and exploring the ethical dimensions of their application.
References:
1. Heckman, K. E., Walsh, M. J., Stech, F. J., O'boyle, T. A., DiCato, S. R., & Herber, A. F. (2015). Active cyber defense with denial and deception: A cyber-wargame experiment. Computers & Security, 37, 72-77.
2. House, C. W., & Cybenko, G. (2010). Hypergame theory applied to cyber attack and defense. Sensors, and Command, Control, Communications, and Intelligence (C3I) Technologies for Homeland Security and Homeland Defense IX, 7666, 766604.
3. Kovach, N. S. (2015). Hypergame theory: A model for conflict, misperception, and deception. Game Theory, 2015, 1-20.
4. Liwanag, J. A., Felizardo, K. R., & Feitosa, E. L. (2022). Artificial intelligence in cyber security: Research challenges and opportunities. ACM Computing Surveys (CSUR), 55(2), 1-36.
5. Vane, R. R. (2005, May). Hypergame theory for DTGT agents. In Proceedings of the 2005 AAAI Spring Symposium on Artificial Intelligence Technologies for Homeland Security (pp. 68-73).





